Do we have a phish for you!
The uptick in cyberattacks in recent months has been so alarming that last week several federal agencies issued alerts, including the FBI, CISA, the White House, and even the Department of Labor got into the act. What has everyone caught in a panic? Let’s just say these aren’t your neighbor’s kids doing the hacking.
It is true that it’s the usual suspects – Russia, China, Iran, and North Korea, but the volume of attacks and the variety of attacks is what has caught everyone’s attention. While phishing attacks (emails with malicious links and/or attachments) still lead the way, we’re seeing a dramatic uptick in vishing attacks as well (phone calls intended to solicit your personal information and often preceded or followed by emails).
The explosion in attacks has long been predicted by the feds and cybersecurity professionals – it’s the adage about success loves company – attacks have been so wildly successful that everyone wants in on the action. Imagine Las Vegas offering 51% odds on all of their tables and slot machines. What do you think would happen? We would all be waiting in line for our seat at the table. Well, in the cybercrime world, there’s no waiting in line and there are seats for anyone willing to fill out a web form to hire a service to launch your very own ransomware campaign. It’s literally that easy.
And these hackers aren’t just mining your social data from LinkedIn, Facebook, and others, they’re also being aided by massive data dumps of stolen passwords. The most recent dump, nicknamed “RockYou2021” by the cybercriminals, included a world record 8.4 BILLION password hacks. In case you didn’t know, there are approximately 4.7 billion online users globally. In other words, there’s almost double the number of passwords in that dataset than there are internet users. Gee, do you think you could be one of them? Wanna make a bet? Check it out here – Have I Been Pwned: Check if your email has been compromised in a data breach. I must confess, yours truly, Jeff Mongelli, has quite a list of stolen passwords. Mind you, most of them are passwords I haven’t used in more than a decade, but among the list of outdated ones are more recent passwords, tied to current email addresses. If not for my password manager, I would have NO IDEA what sites are tied to that email and password combination so I could change it. So once again I implore you, I beg you, to get a password manager like LastPass or Roboform for example. If you’re dealing in sensitive data online and you aren’t using one, then at this point you’re truly being negligent. Sorry to be so blunt, but we’ve reached that point.
The truth is not only are errant clicks on EXTREMELY CLEVER fake emails costing us (as in the US) our treasury but so is our ignorance when it comes to password management. One errant click, one compromised password, can expose your entire organization to a cyber-attack. Johnny receptionist clicks a link in an email for job posting, unbeknownst to Johnny software is downloaded and hackers hop into his machine and quickly promote his user level to super admin using special software. The next day, your entire organization experiences a ransomware attack and all of the computers are locked down. THIS is what’s happening EVERY DAY.
But Jeff, you say, this is only happening to large companies, not companies like us. Here’s a healthcare graphic provided courtesy of the National Cyber-Forensics & Training Alliance (NCFTA):
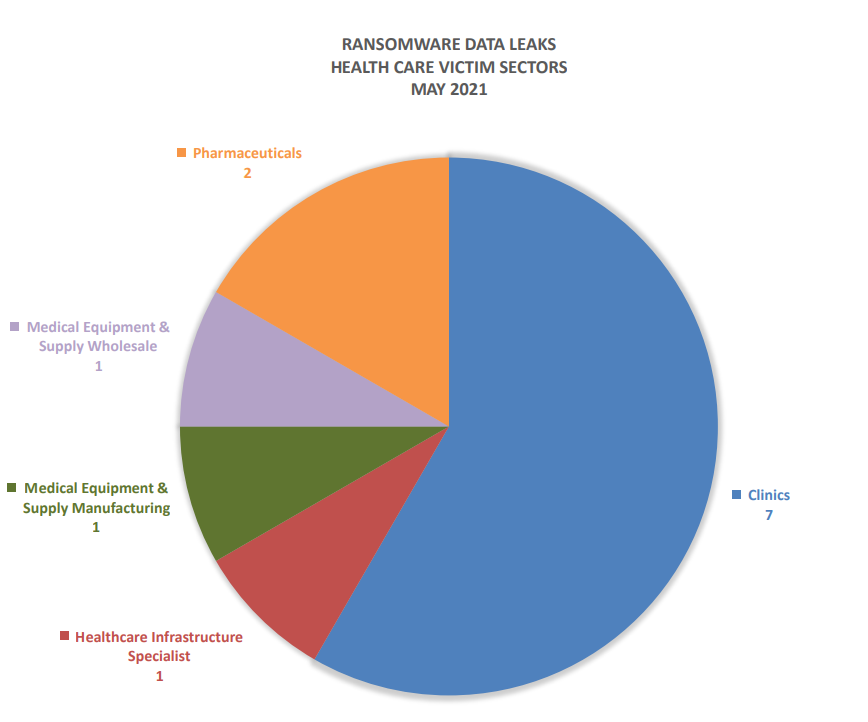
Notice the distribution of attacks – clinics – most of them small businesses, are getting hammered. Why? Small businesses are the least prepared and have limited resources to fight off or recover from an attack, so they’re more likely to pay the ransom. With a 2020 average ransomware payout of over $200,000, most of us would take that as a daily paycheck any day of the week.
Look, these phishing emails have gotten so good I catch myself with my finger on the mouse button. And the vishing calls are equally clever and deceptive. Yes, that recruiter calling you about this dream job is actually after your personal info, and they can easily spoof their phone number to look like a recruiting company.
If you’re bound by HIPAA, then you need to be training your employees at least once a year. If you think that’s enough, it’s not. Things are changing so rapidly you should have a training queued up for your staff monthly. Even little pain in the neck reminders like this will help keep them alert.
We are at war, folks. And we are losing. Please step up your game when it comes to your technology, your social media awareness, and your personal device use. We can help. Call us.
BTW, if you use Alexa and/or Ring, you have to disable Sidewalk in BOTH applications. USe DuckDuckGo to search for how or call us to walk through it. Amazon didn’t make shutting it off obvious.
It’s a beautiful summer. Be sure to enjoy it AFTER you implement a password manager. 😉
If you have any questions or if you are concerned about your organization’s cybersecurity, give us a call at (800) 970-0402. We’ll be happy to help.
For more HIPAA information, download our ebook – The Ultimate HIPAA Compliance Handbook.
The HIPAA Security Rule requires the implementation of a security awareness and training program for all members of its workforce (including management). Have your team sign up for a weekly HIPAA Security Reminder to help stay compliant.
